In the past few weeks, there have been hundreds of fake retail and product applications in Apple’s App Store. The fake apps have pretended to be companies such as Dollar Tree, Foot Locker, Nordstrom, and Dillard’s. A company that tracks new shopping apps, Branding Brand, reported a large increase in these fake applications in the past few weeks.
The apps are being created to trick Black Friday shoppers into clicking them. Some apps seem to be harmless, just displaying pop-up ads whenever users click on them. Others, however, are dangerous because users can have their credit card information stolen if the app asks them to input it. Also, some of the apps can contain malware that can steal personal information and even lock the victim’s phone.
The fake apps came from developers in China; they were somehow able to get past Apple’s review process for new apps. Apple’s app screening process is less strict than Android’s; Apple focuses more on blocking malicious software and does not routinely examine the thousands of new apps that are sent to them everyday. It is important for brands and companies themselves to search for and report these fake apps, similar to how they search for and report fake websites. Last week, however, Apple did remove hundreds of fake apps after an article was published about the apps. A spokesperson for Apple claims that they have set up ways for customers to report fake apps. In September, Apple started to look through their two million apps to remove fake and unnecessary ones. Despite this, new fake apps continue to appear.
A recent example of a fake app was one called Overstock Inc. – apparently named to let customers believe that it was the real company app for Overstock.com. The developer of the app is the Chinese company Cloaker Apps. The CEO of Cloaker, Jack Lin, claims that the company only provides the back-end technology for the apps; they do not investigate their clients. However, not even Cloaker is what it seems; the company’s website states that its headquarters is in the middle of Facebook’s campus in Menlo Park, California. When Jack Lin was first interviewed, he claimed that the company only had offices in China and Japan. When asked about the office in California, he claimed to have “tens of employees” there.
China is, by far, the biggest source of fake applications. Many of the fake apps have red flags to show that they are not real, including: nonsensical menus in broken English, no reviews, and no history of previous versions of the app. So far, thousands of individuals have apparently fallen prey to the newest fake apps. However, in most cases, no serious problems have occurred. The fake apps usually target companies either with no apps or multiple apps. Some have even used Apple’s paid search ads to put their fake apps at the top of the search results.
Fake apps on Apple are a new problem, occurring more commonly in the past few months. However, with Black Friday soon approaching, it is important to remember to check the applications that you are planning to download. Also, if possible, try to use alternative methods to applications that ask for banking or personal information. For example, try to use the company’s website on your laptop or computer; also, remember to check the security on the website itself. Criminals are obviously going to take advantage of whatever situation becomes available to them. Therefore, you should always be careful of what you click or download on your phone or computer.
Article Link: Beware, iPhone Users

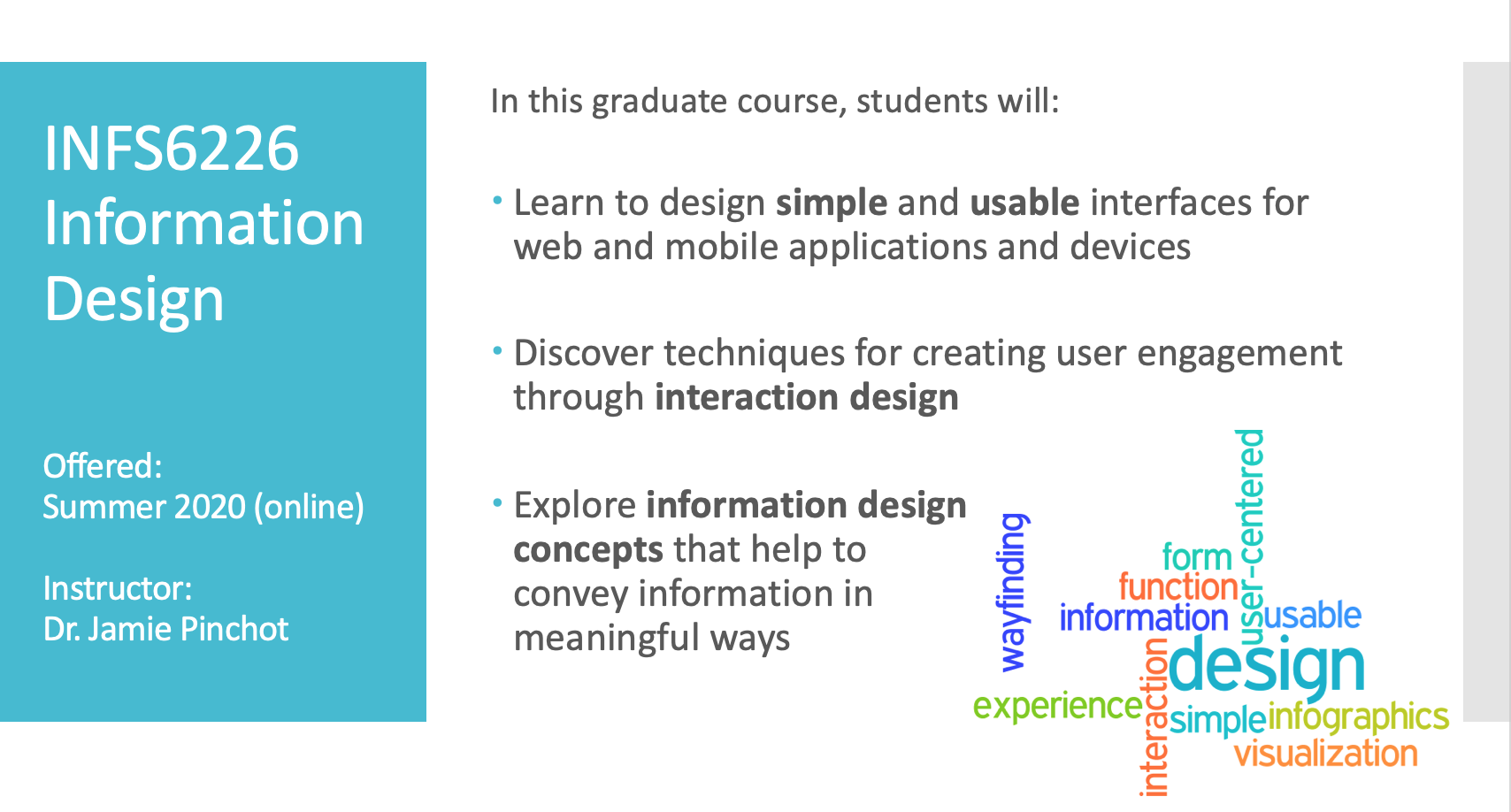
 On April 24, 2017, RMU held a Research & Grants Expo highlighting a variety of faculty research and grant projects. All of the RMU campus was invited to attend this event. Dr. Karen Paullet presented the Mobile Forensics and Security Project, an NSF-funded grant. Dr. Paullet is the PI on the grant, along with Dr. Jamie Pinchot (Co-PI), Dr. Sushma Mishra (Co-PI), and Dr. Fred Kohun. Mobile security and forensics is an underrepresented area of study that is increasingly important in our current society. This research will advance knowledge in the field of mobile cybersecurity and mobile forensics through a train-the-trainer program for 50 faculty members from universities across the United States. Twenty-five faculty were trained in July 2016 and the remaining half will be trained this year. Dr. Paullet also highlighted a new online certificate offered by RMU in Mobile Forensics and Security (MFS). This certificate is now available and you can learn more about it here:
On April 24, 2017, RMU held a Research & Grants Expo highlighting a variety of faculty research and grant projects. All of the RMU campus was invited to attend this event. Dr. Karen Paullet presented the Mobile Forensics and Security Project, an NSF-funded grant. Dr. Paullet is the PI on the grant, along with Dr. Jamie Pinchot (Co-PI), Dr. Sushma Mishra (Co-PI), and Dr. Fred Kohun. Mobile security and forensics is an underrepresented area of study that is increasingly important in our current society. This research will advance knowledge in the field of mobile cybersecurity and mobile forensics through a train-the-trainer program for 50 faculty members from universities across the United States. Twenty-five faculty were trained in July 2016 and the remaining half will be trained this year. Dr. Paullet also highlighted a new online certificate offered by RMU in Mobile Forensics and Security (MFS). This certificate is now available and you can learn more about it here: 